Three years ago I wrote a document titled “Removing Exchange’s ability to impact Tier 0 and Tier 1” that was…
I had an interesting request at work today. Management wanted all employees with a company issued cell phone, to have…
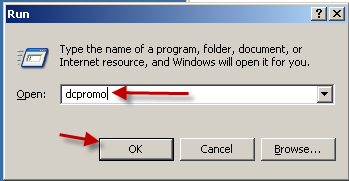
I know what you're thinking, it's 2011, Windows Server 2008 R2 has been out for years, why are you writing…